Since the introduction of modern computers, malicious software or malware has been an omnipresent issue. Viruses, Trojans, rootkits, spyware, keyloggers and several others of the like continue to assault your computing devices all the time, looking for vulnerabilities and loopholes in your defenses to get through. Generally, users have become aware enough to deploy some form of protection on their desktops and notebooks, and while infections continue to plague the computing world, they’re significantly reduced in impact. Smartphones today are nothing short of portable computers as well, and just like that, are prone to malware attacks. Hard as it may seem to believe, developers do spend time creating Smartphone malware that would let them access your personal information, exploit personal data and otherwise do damage to your device. Android Device is a fast-growing mobile platform with apps exceeding 600,000 in the Google Play Store, and believe me when I tell you that an assessment puts over 100,000 of them as “questionable”. While most users don’t pay much attention to it, it’s imperative that you secure your Android smartphone or tablet against the growing threat of mobile malware. They say prevention is better than cure, and in this post, we’ll provide some basic pointers on how to achieve that.
Ways to Keep your Android/Tablet Device Secure
There are easy ways to reduce the risk of infection in your Android. Most of these ways are simply common sense. Developers and specific cell phone manufacturers do encourage their customers to use the proper download applications and widgets.
1. Download Only From Official Stores
When downloading apps, prefer the well-reputed channels, mainly Google Play Store and the Amazon App Store. Google implements a rudimentary “bouncer” to ward off malware, and the rest is taken care of by the very active Android user community. Hence, these two sources are your most reliable ones.

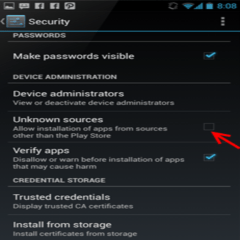
2. Keep Installation of Apps from Unknown Sources at “Off”
Unless you’re a power user, it’s highly advisable to keepthe installation of apps from Unknown Sources at “off” in the device’s settings. This will help ensure that nothing enters the system except through official channels.
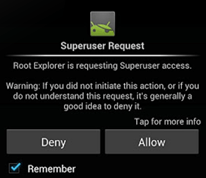
3. Rooted Devices are More Susceptible
Most advanced users choose to root their Android devices, be extra cautious about granting Superuser access to any app. Make sure you understand the purpose of the SU access and trust the developer enough to grant it. This is the highest level of access that anyone (or anything) can have on your Android device, so be really careful with this one.
4. Install an Antivirus/Security App on Your Android Smartphone
A lot of capable contenders are available in the Google Play Store for that purpose, with more notable ones being Avast! Free Mobile Security, Lookout Mobile Security, AVG Mobile Security, Kaspersky, and Norton Mobile Security, just to name a few. There is a different feature-set offered by each, so you have room to weigh your options carefully before making a decision to go with one.

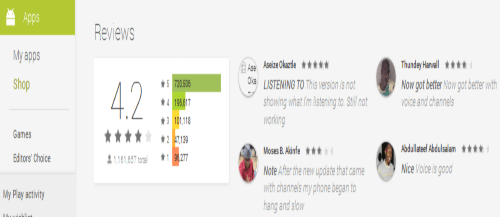
5. It is Important to Read App reviews and See ratings before downloading
Read app reviews and see ratings before you choose to download anything. If it’s something from a renowned developer, you’re less likely to run into trouble as opposed to an app with hardly any downloads and just 2-3 reviews. As a rule of thumb, I don’t prefer apps with a rating of less than at least 3 stars.
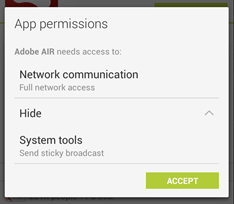
6. Examine the Permissions that an App is Asking For, During Installation
Carefully examine the permissions that an app is asking for, and use your own judgment to decide whether you want that app or not. E.g A puzzle game asking to access your contacts and the phone app is never really a good idea, and neither is a torch app seeking internet permission. Discard apps that seem shady – they’re usually not worth risking personal information over.
7. Keep Your Phone Locked Always
While not strictly a malware protection measure, it’s still a good idea to keep your phone locked for security. Someone else gaining access to your device might be able to install undesired software before you reclaim access, and hence, causing you to remain unaware of the whole deal until it’s too late. Likewise, a remote wipe app should also be there, should you ever encounter a scenario where normal access to the device gets blocked by the malware infection.
8. Never access links embedded in mass-broadcast messages/emails on your phone.
You never know what’s hidden underneath a URL, and it’s harder to check that on a Smartphone as opposed to a traditional computer. Phishing scams thrive under unrestricted access through your web browser.
9. Beware of Fake Apps Even on Play Store
On the Play Store, there are loads of fake apps designed with the intention of infecting your device and stealing your private information. Some apps are designed only to push ads to your Smartphone. As a matter of fact, most popular apps often have similar ones that are actually fake. You should be careful with these sorts of apps.
10. Avoid Pirated Apps
If you love the cracks and pirated apps, your device may become infected without you even knowing it. Pirated apps most often carry Malware strands. Besides, you’re not helping the developers who work hard trying to create these games and apps. Saving $0.99 isn’t worth it, really.
11. Porn is the Most Efficient Source of Malware Delivery
I’m in no position to judge you or tell you what to do with your device, but it has been proven that pornographic sites are the most efficient when it comes to infecting your device with malware. Well, you know what to do… be careful with sites you visit.
12. Stay Updated
Be on your toes so far as updates are concerned. This is one way in which manufacturers and carriers ensure that you remain protected from Malware attacks. These updates can include enhancements, bug fixes, new features each of which are designed to keep your system in tune with the right way to tackle the malicious attacks. Apart from updating your apps, be sure your device operating system is also up-to-date. Conclusion Following the above steps will help you ensure that your device remains secure, safe from malware, and most importantly, exclusively yours. Do you have a tip that we should’ve included here and missed? Drop us a comment below.